Cybersecurity services
Elevate your business with our cybersecurity solutions, designed to meet international standards, safeguard your digital assets, and boost your reputation and operational strength
Penetration testing
In an increasingly digital world, cybersecurity has become a cornerstone of any successful business. Our Penetration Testing Services are designed to safeguard your organization’s critical systems, data, and applications by identifying vulnerabilities before malicious actors can exploit them.

Penetration testing, or ethical hacking, is a proactive approach to cybersecurity. It involves simulating real-world attacks on your IT infrastructure to uncover potential weaknesses. By doing so, we help you understand where your defences stand and provide actionable insights to strengthen them.
- Comprehensive Testing: Our experts employ advanced tools and techniques to analyze networks, applications, and systems for vulnerabilities.
- Real-World Simulations: We mimic the tactics and strategies of actual hackers to test your defences effectively.
- Detailed Reporting: Receive in-depth reports outlining vulnerabilities, their impact, and practical recommendations for mitigation.
- Certified Professionals: Our team includes certified ethical hackers (CEH), offensive security experts, and experienced cybersecurity professionals.
- Regulatory Compliance: Ensure your business meets industry standards such as GDPR, PCI-DSS, and HIPAA.
- Scoping: We collaborate with you to understand your systems and define testing goals.
- Reconnaissance: Gathering information about your network, applications, and systems to plan effective tests.
- Vulnerability Identification: Utilizing cutting-edge tools and techniques to uncover weaknesses.
- Exploitation: Attempting to exploit identified vulnerabilities to assess their real-world risk.
- Reporting and Remediation: Delivering a detailed report with insights, risk assessments, and recommendations.
- Network Penetration Testing: Identifies vulnerabilities in your wired and wireless networks.
- Web Application Testing: Secures your websites and applications against threats like SQL injection, XSS, and more.
- Mobile Application Testing: Ensures your mobile apps are safe from potential breaches.
- Cloud Security Testing: Protects cloud-based systems from misconfigurations and vulnerabilities.
Enhance security posture by identifying and addressing risks. Prevent costly data breaches and downtime. Build trust with customers and stakeholders by demonstrating commitment to security. Gain a competitive edge with robust cybersecurity measures.
Vulnerability Assessments
In today’s fast-evolving digital landscape, staying one step ahead of cyber threats is crucial. Our Vulnerability Assessment Services provide a detailed evaluation of your organization’s IT infrastructure, helping you identify and address potential weaknesses before they become critical issues.
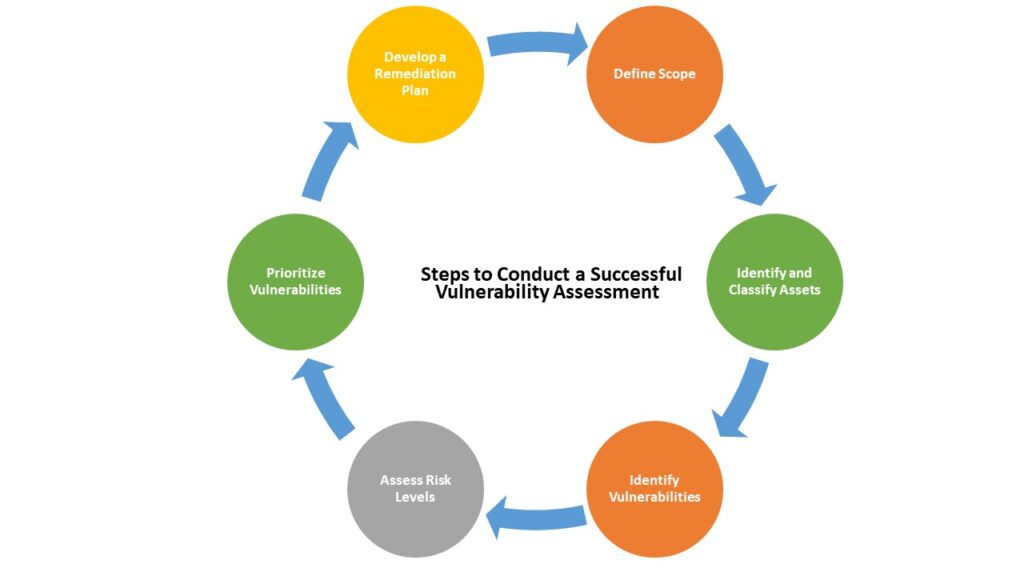
A vulnerability assessment systematically reviews your systems, networks, and applications to detect potential security flaws. Unlike penetration testing, which focuses on exploiting vulnerabilities, this service prioritizes identifying and categorizing risks to prioritize remediation efforts effectively.
- Thorough Scanning: Using state-of-the-art tools, we examine every aspect of your IT infrastructure to uncover hidden vulnerabilities.
- Risk Prioritization: Our team evaluates the severity of identified vulnerabilities and recommends actionable solutions.
- Expert Insight: Benefit from a dedicated team of cybersecurity professionals with extensive experience.
- Regular Assessments: Ensure ongoing security with routine evaluations tailored to your business needs.
- Compliance Support: Achieve and maintain compliance with standards such as ISO 27001, PCI-DSS, and more.
- Scope Definition: Collaborate with our team to define the systems and networks to be assessed.
- Scanning: Use automated and manual techniques to identify vulnerabilities across your IT assets.
- Analysis: Examine the results to evaluate risks based on potential impact and likelihood of exploitation.
- Reporting: Provide a detailed report, including an executive summary, technical findings, and prioritized recommendations.
- Follow-Up: Offer guidance on implementing remediation strategies and retesting for assurance.
- Network Vulnerabilities: Identify risks such as misconfigured firewalls, open ports, and unpatched systems.
- Application Vulnerabilities: Detect issues like outdated software, insecure coding practices, and improper access controls.
- System Configurations: Evaluate servers, databases, and devices for weak configurations and permissions.
- Cloud Environments: Assess cloud services for security gaps, misconfigurations, and compliance risks.
- Endpoint Security: Ensure desktops, laptops, and mobile devices are adequately protected against threats.
- Proactive Risk Management: Address vulnerabilities before they can be exploited.
- Cost-Effective Security: Avoid costly breaches and downtime with early detection and resolution.
- Enhanced Compliance: Meet regulatory and industry standards with a well-documented security posture.
- Improved Incident Response: Strengthen your team’s ability to respond to potential threats effectively.
Protecting your organization begins with understanding its vulnerabilities. Let us help you build a strong foundation for cybersecurity. Contact us today to schedule your vulnerability assessment!
Incident Response
When a cyberattack strikes, every second counts. Our Incident Response Services are designed to help organizations effectively manage and mitigate cybersecurity incidents, minimizing damage and ensuring a swift recovery. With a team of seasoned experts, we stand ready to safeguard your business against evolving threats.

Incident response is a structured approach to detecting, responding to, and recovering from security incidents. This includes cyberattacks, data breaches, and other critical events that could compromise your organization’s operations, data, or reputation. Our services ensure that you have a well-prepared plan and the expertise needed to handle incidents efficiently.
- Rapid Response: Immediate action to contain and mitigate threats as soon as they are detected.
- Experienced Team: Certified incident response professionals with extensive expertise in handling complex incidents.
- Comprehensive Solutions: From containment to recovery, we manage every step of the incident lifecycle.
- 24/7 Availability: Around-the-clock support to ensure your business is protected at all times.
- Post-Incident Support: In-depth analysis and recommendations to prevent future incidents.
- Preparation: Work with your team to create or refine an incident response plan tailored to your organization.
- Detection and Analysis: Identify and assess the nature and scope of the incident using advanced tools and techniques.
- Containment: Quickly isolate affected systems to prevent further damage and secure critical assets.
- Eradication: Remove malicious threats and address vulnerabilities exploited during the incident.
- Recovery: Restore systems, applications, and data to full operational status with minimal downtime.
- Post-Incident Review: Conduct a detailed analysis to understand the root cause, evaluate the response, and implement preventive measures.
Malware infections and ransomware attacks Data breaches and unauthorized access Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks Insider threats and employee misconduct Phishing and social engineering attacks Cloud and SaaS-related incidents
- Minimize Downtime: Swift action reduces the impact on your operations and revenue.
- Protect Your Reputation: Demonstrate strong security practices to maintain customer and stakeholder trust.
- Comprehensive Support: Guidance through every phase, from detection to prevention.
- Regulatory Compliance: Ensure adherence to legal and industry requirements during and after an incident.
- Proactive Insights: Learn from each incident to strengthen your cybersecurity defences.
Don’t wait until it’s too late—prepare for the unexpected with our expert incident response services. Contact us today to build a resilient defense against cyber threats!
Threat Intelligence
In the rapidly changing world of cybersecurity, staying ahead of emerging threats is critical. Our Threat Intelligence Services empower your organization with actionable insights to identify, understand, and mitigate potential cyber threats before they materialize.

Threat intelligence involves gathering, analyzing, and sharing information about current and emerging cybersecurity threats. This proactive approach helps organizations anticipate risks and respond effectively, reducing their exposure to potential attacks.
- Real-Time Insights: Gain up-to-the-minute information on global threat landscapes.
- Actionable Intelligence: Receive clear, prioritized recommendations tailored to your organization’s needs.
- Expert Analysts: Our team of cybersecurity specialist leverages advanced tools and techniques to deliver accurate intelligence.
- Industry-Specific Focus: Customized insights based on the unique challenges of your sector.
- Integration with Security Operations: Enhance your existing defences by embedding threat intelligence into your security workflows.
- Data Collection: We gather information from a variety of sources, including open-source data, threat feeds, the dark web, and industry reports.
- Threat Analysis: Our experts analyze and contextualize the data to uncover patterns, trends, and potential risks.
- Reporting: Provide detailed, easy-to-understand reports with insights, threat assessments, and mitigation strategies.
- Continuous Monitoring: Stay protected with ongoing threat tracking and timely alerts.
- Collaboration: Work closely with your team to implement intelligence findings into your security posture.
- Strategic Threat Intelligence: Long-term insights to shape your security strategy and policy decisions.
- Tactical Threat Intelligence: Practical guidance on specific threats, such as malware, phishing campaigns, or ransomware.
- Operational Threat Intelligence: Real-time alerts and recommendations for immediate action.
- Threat Actor Profiling: In-depth analysis of attackers, their motivations, and methods.
- Dark Web Monitoring: Keep track of data leaks, compromised credentials, and potential targeting on hidden forums and markets
- Proactive Defence: Anticipate and prevent threats before they impact your business.
- Informed Decision-Making: Equip your security team with data-driven insights for effective risk management.
- Enhanced Security Posture: Strengthen your defences with a deeper understanding of the threat landscape.
- Reduced Response Time: Respond swiftly and accurately to emerging threats.
- Compliance Support: Stay aligned with regulatory and industry standards by demonstrating robust threat management practices.
Stay ahead in the battle against cyber threats. With our threat intelligence services, you can protect your organization with foresight and confidence. Contact us today to learn more!
Managed Security Services
In an era where cyber threats are becoming more sophisticated and frequent, maintaining a robust security posture can be challenging. Our Managed Security Services (MSS) provide a comprehensive, 24/7 solution to protect your organization’s digital assets, allowing you to focus on your core business activities with peace of mind.

Managed Security Services involve outsourcing your cybersecurity operations to a team of experts who monitor, manage, and improve your security infrastructure. These services are designed to prevent, detect, and respond to cyber threats while ensuring your organization stays compliant with regulatory standards.
- 24/7 Monitoring: Round-the-clock surveillance of your IT environment to detect and respond to threats in real time.
- Expert Team: Certified cybersecurity professionals with expertise across various industries and technologies.
- Cost-Effective Solutions: Reduce the expense of maintaining an in-house security team while gaining access to top-tier talent.
- Scalable Services: Tailored solutions that grow with your business needs.
- Advanced Tools: Leverage cutting-edge technologies for threat detection, response, and prevention.
- Security Operations Centre (SOC): Our dedicated SOC provides real-time threat monitoring, analysis, and response.
- Endpoint Detection and Response (EDR): Protect your devices from malware, ransomware, and other endpoint-specific threats.
- Firewall Management: Ensure your network defences are configured and updated to block malicious activity effectively.
- Threat Detection and Incident Response: Rapid identification and containment of potential security breaches.
- Vulnerability Management: Regular scans and patch management to keep your systems secure.
- Compliance Management: Assistance with meeting regulatory standards such as GDPR, HIPAA, and PCI-DSS.
- Dark Web Monitoring: Keep an eye on potential leaks or breaches involving your organization’s data.
- Enhanced Protection: Detect and neutralize threats before they impact your business.
- Reduced Complexity: Simplify security management by outsourcing to experts.
- Business Continuity: Minimize downtime and disruption with rapid threat response.
- Regulatory Compliance: Demonstrate strong security practices to auditors and regulators.
- Peace of Mind: Focus on your business while we handle your cybersecurity needs.
- Proven Expertise: Years of experience delivering managed security services across diverse industries.
- Customized Approach: We tailor our services to meet the unique needs of your organization.
- Transparent Reporting: Regular updates and detailed reports keep you informed about your security status.
- Customer-Centric Service: A dedicated account manager ensures seamless communication and support.
Let us take the complexity out of cybersecurity with our managed security services. Protect your organization’s data, reputation, and operations with confidence. Contact us today to secure your business for the future!
Get in Touch
Fill in this form below to book a 30min no-obligation consulting session.
We will reply within 24 hours.
Industry We Serve





